Configuring Discovery Search with Microsoft Azure Active Directory
Connecting Discovery Search to Microsoft Azure Active Directory is required before connecting Microsoft SharePoint Online and Microsoft Exchange Online.
Connecting Discovery Search to Microsoft Azure Directory
Before configuring Azure AD in Discovery Search, administrators must register and authenticate the Discovery Search app with the Azure Portal.
Registering the Discovery Search App
Open a browser and navigate to the Azure Portal (Microsoft Azure Portal)
Select Azure Active Directory on the homepage
Select App Registrations from the navigation panel in Azure AD
Click + New Registration to add a new App Registration
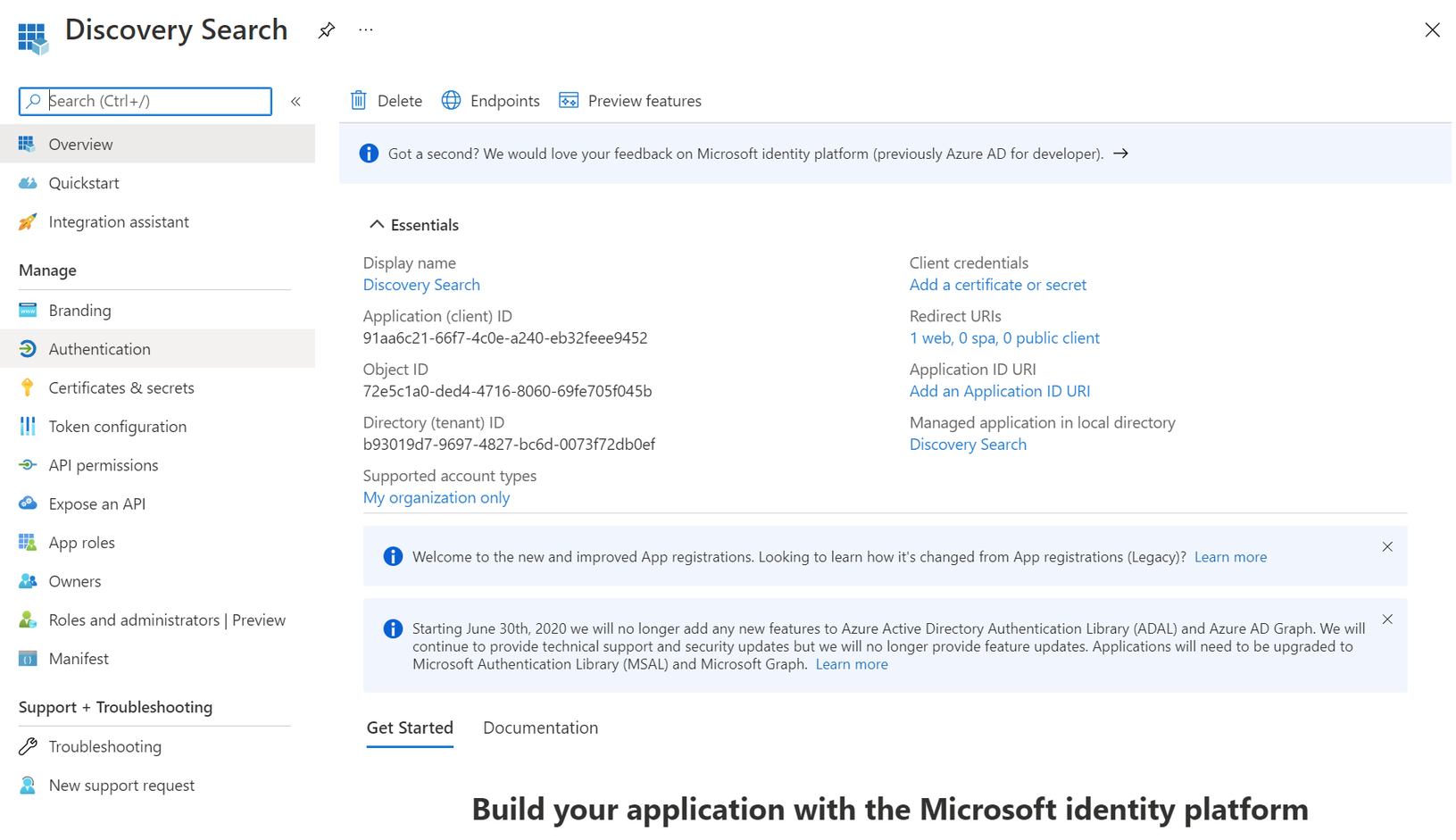
On the Register Page, you will need to provide the following information:
Name: This is a display name for the application. It is used to identify what the application is used for, so make it descriptive.
Supported Account Types: This should be Accounts in this organizational directory only (Single tenant). This limits logins to the organization that is using the SharePoint instance.
Redirect URI: This is the URL that Azure should redirect to once the login is successful. Typically this should be your Discovery Search app’s fully qualified domain name. If you are using a load balancer, it should be the URI used to hit it, not the individual machines behind it.
Click Register
Setting up Authentication
Click the Authentication link on the navigation sidebar
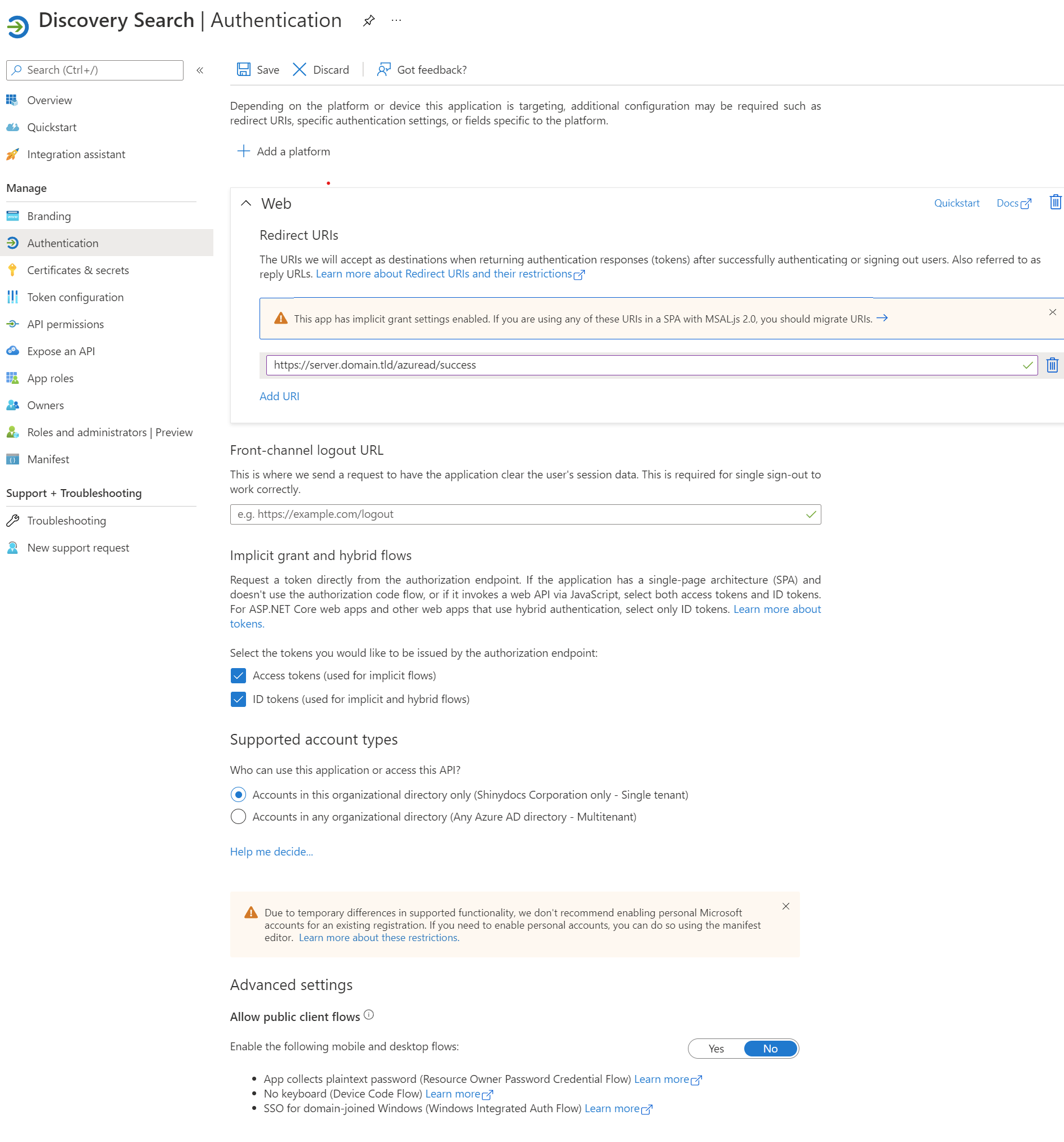
Make the following changes on the Authentication page:
Redirect URIs: This should be the URI to the Discovery Search server, including the /azuread/success path (for example, https://search.domain.com/azuread/success)
Select both Access tokens and ID tokens in the Implicit Grant and Hybrid Flows section
Front-channel logout URL: This can remain empty
Ensure Supported account types is set to Accounts in this organizational directory only (single tenant)
Advanced settings - Allow public client flows: This should be set to No
Save changes if required
Adding a Client Secret
This section describes how to add a secret to the app registration.
From the App page, select Certificates & secrets from the navigation sidebar
Click + New client secret on the Client secrets tab
Provide the following information on the form
Description: A descriptive name of the secret
Expires: Provide how long the secret is valid. Note that, when it expires, the integration with Discovery Search stops working until a new secret is generated and updated in the Discovery Search web.config file
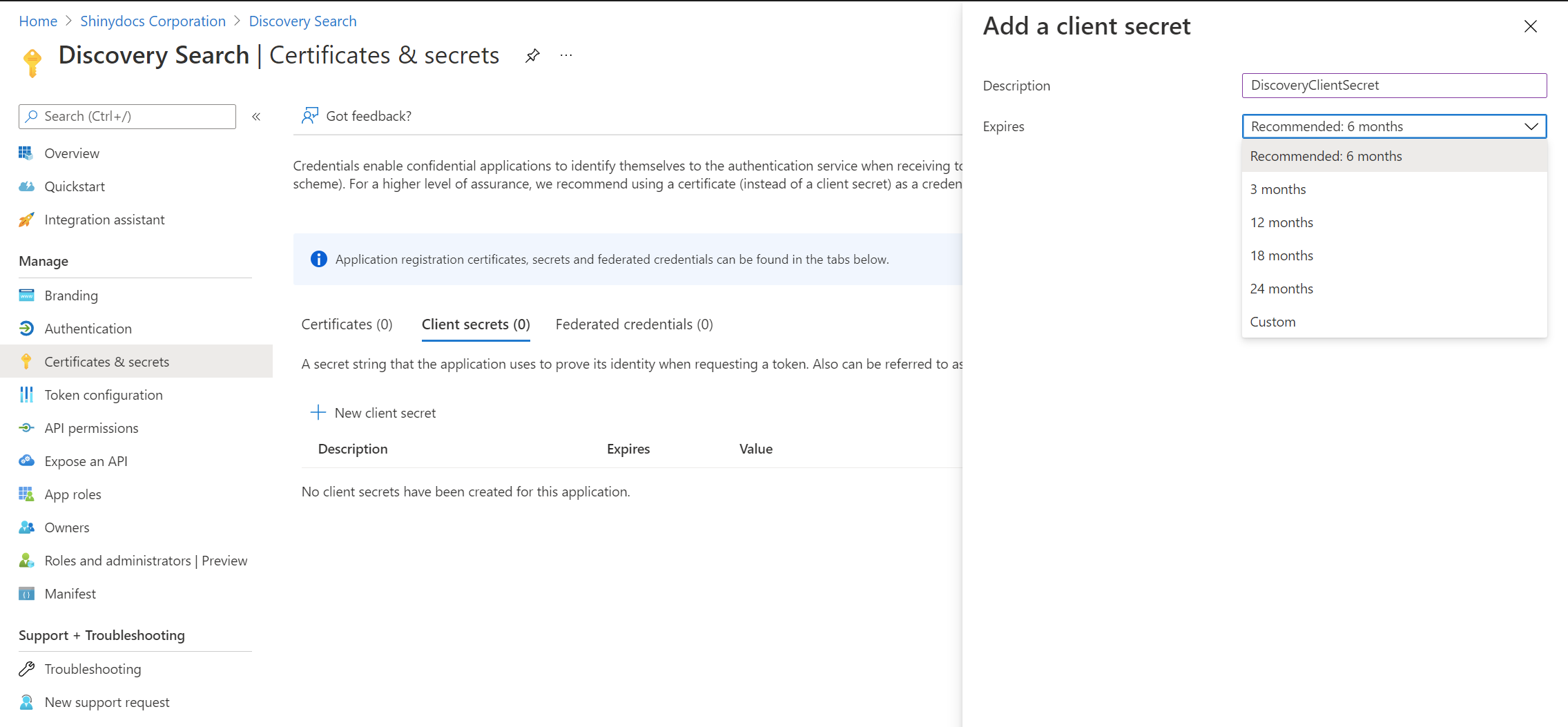
Click Add at the bottom of the screen
Copy the value for the secret shown on the page for safekeeping. This is the only time you will be able to see it, and this will be needed as part of the configuration for Discovery Search.
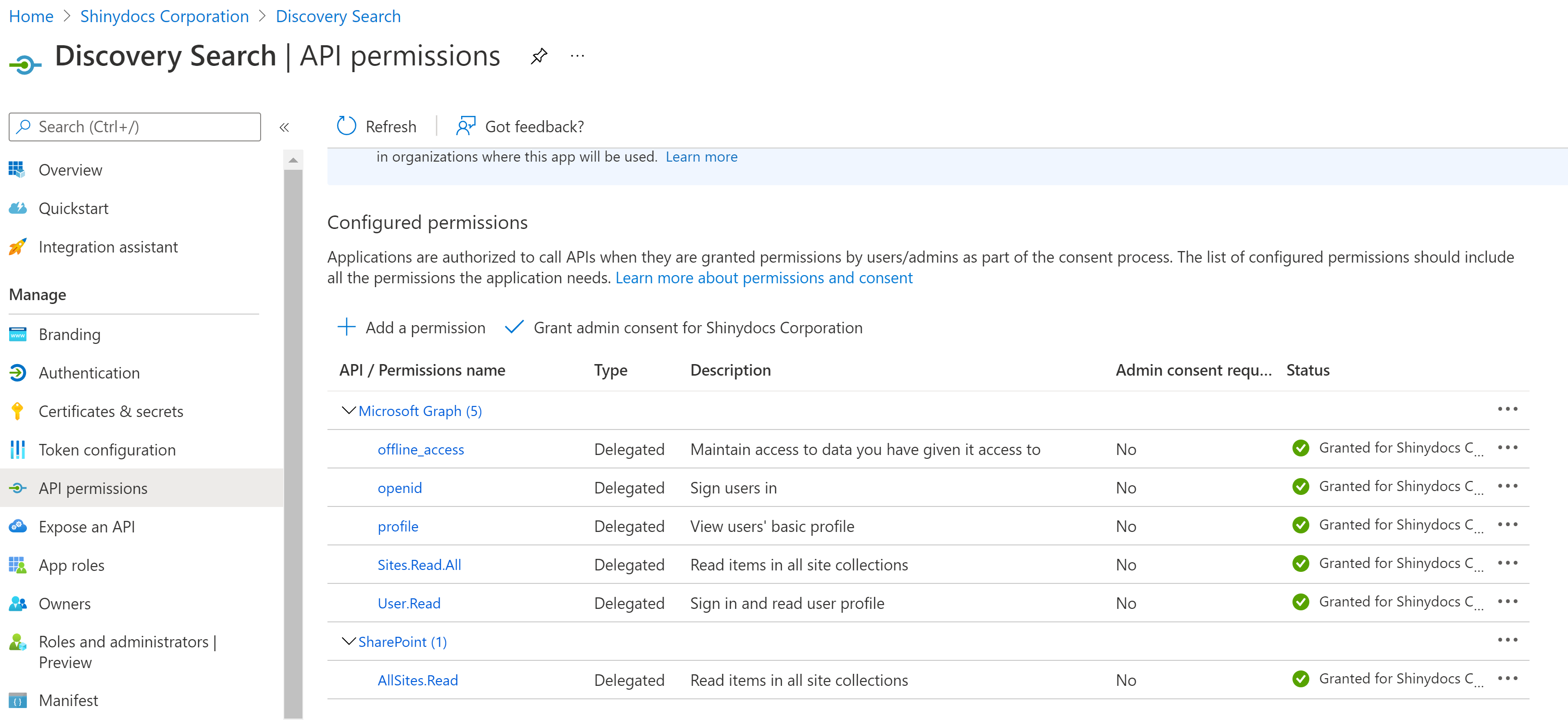
Setting up API Permissions
This section describes how to set up the appropriate API permissions for this application. This will allow Discovery Search to access SharePoint Online as the delegated user to do a permissions check.
Select API permissions from the App registration navigation sidebar
Click + Add a permission
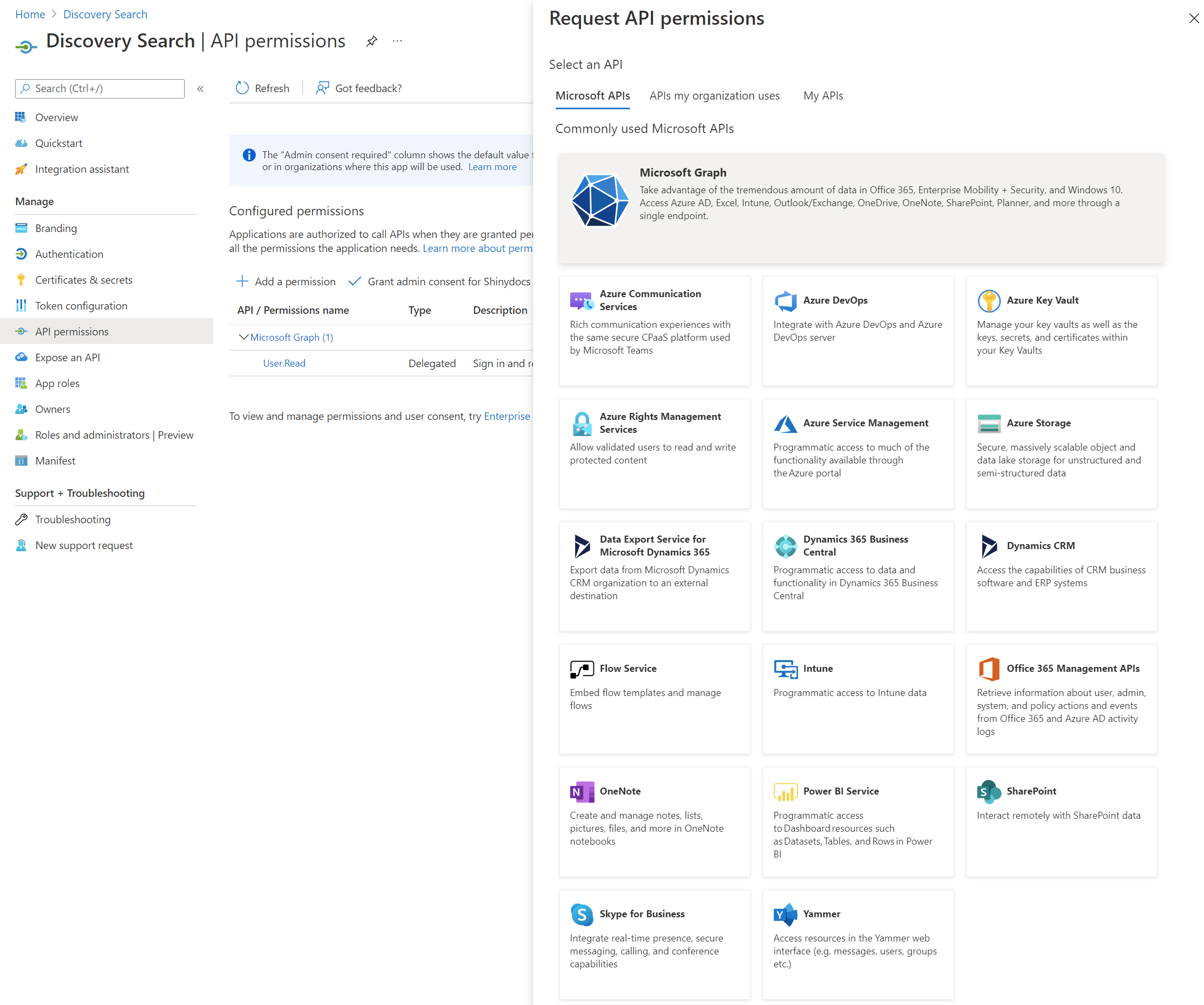
Select Microsoft Graph and then select Delegated permissions (Your application needs to access the API as the signed-in user)
offline_access: This is used to generate an OAuth refresh token so that users do not need to authenticate for each search request
openid: Allows users to sign in to Azure AD
profile: Allows users to sign into Azure AD
User.Read: Allows users to sign into Azure AD
Click Add permissions
Click + Add a permission again
Select SharePoint and then select Delegated permissions (Your application needs to access the API as the signed-in user)
AllSites.Read: This allows signed-in users to view any sites and their contents to which they have access. This also allows Discovery Search to execute the permissions check.
Click Add permissions
Click Grant admin consent for <Organization Name>
The final result should look like this:
Configuring Azure Active Directory in Discovery Search
This section describes how to configure Discovery Search to authenticate against Azure AD, enabling the search of SharePoint Online and Exchange Online.
Open Discovery Search Admin
Select Application settings at the bottom of the navigation sidebar
Select Microsoft® Online settings
Fill in the following settings
Azure AD client ID: This can be found on the overview page of the App registration in the Azure portal.
Azure AD tenant ID: This can be found on the overview page of the App registration in the Azure portal.
Azure AD secret: This is the value of the secret that was created above. If you did not copy it at the time, you will need to create a new one.
Azure AD Redirect URL: This is the URL that Azure AD will redirect to once the user is authenticated properly. This should be in the form of http://server/azuread/success. This should match the one added to the Authentication page in the Azure portal as documented above.
Save changes
Restart the Discovery Search application in IIS
