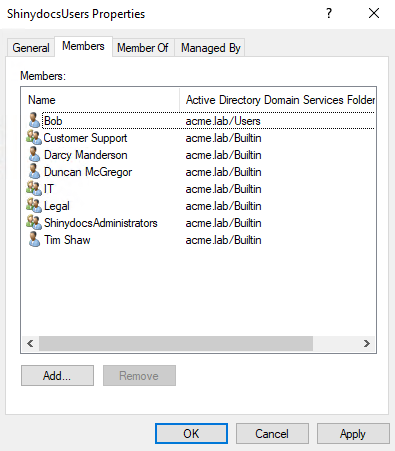
Role-Based Access (RBAC) in Shinydocs Pro Control Center
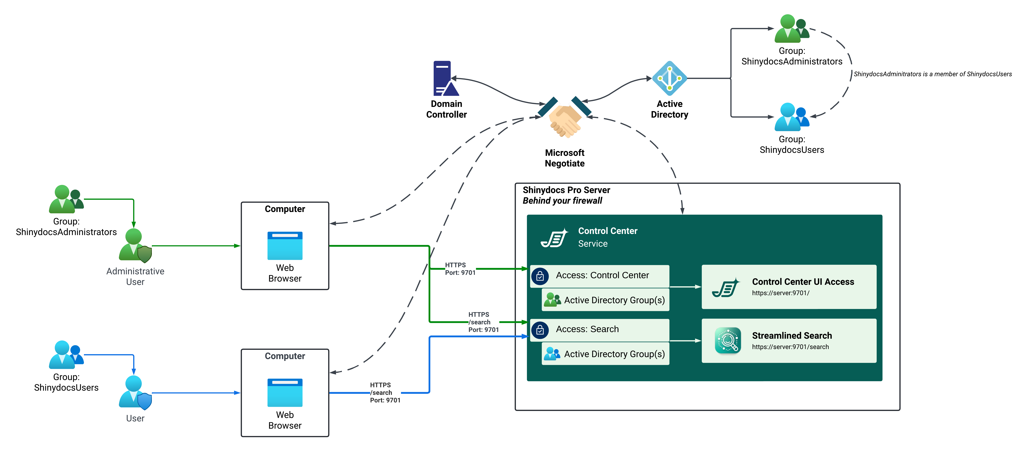
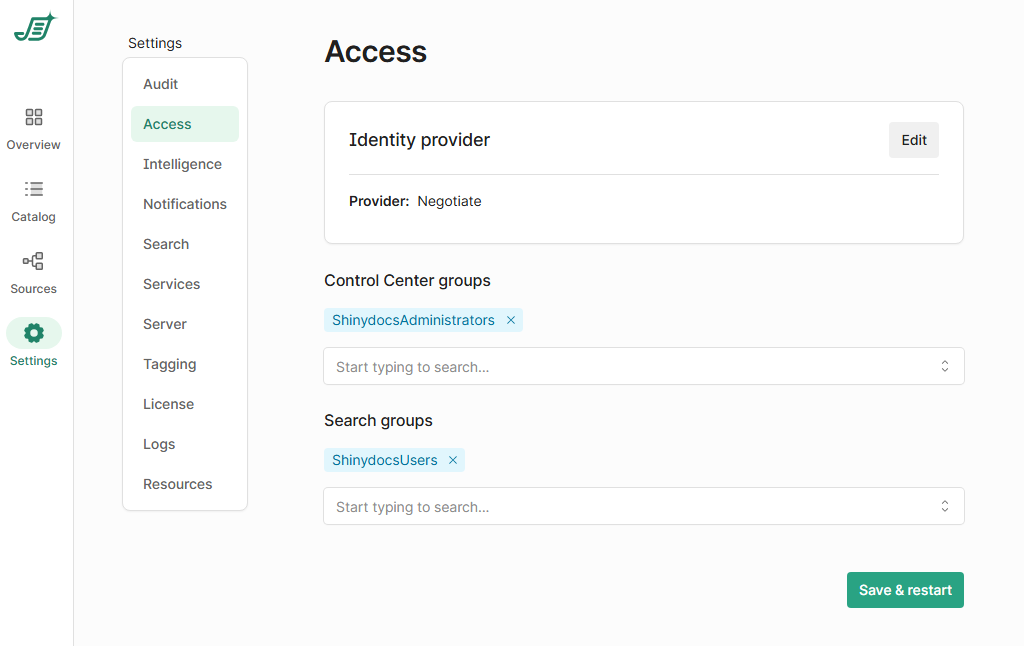
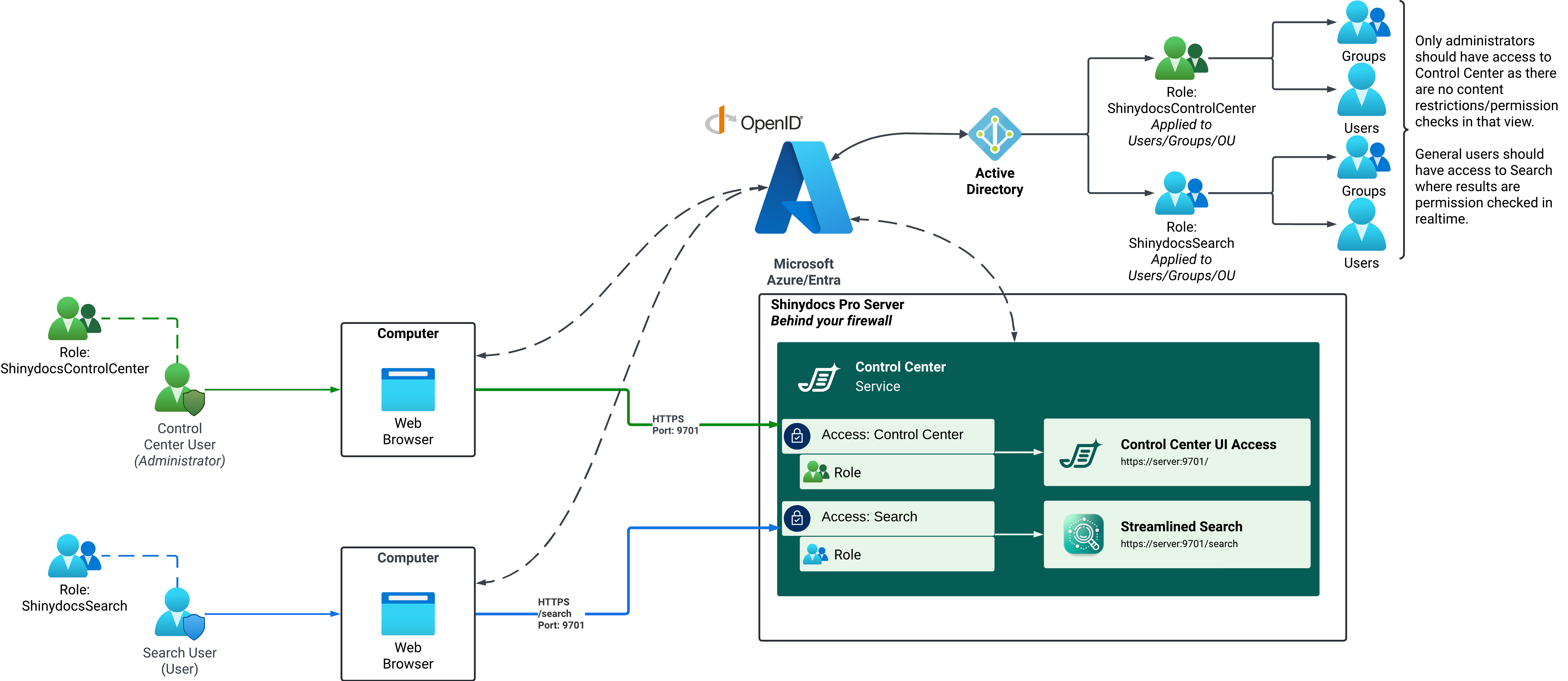
Role-Based Access Control (RBAC) is used to control access to Shinydocs Pro Control Center. This allows administrators to manage access by assigning roles to users or groups, ensuring that only authorized users can access the Control Center.
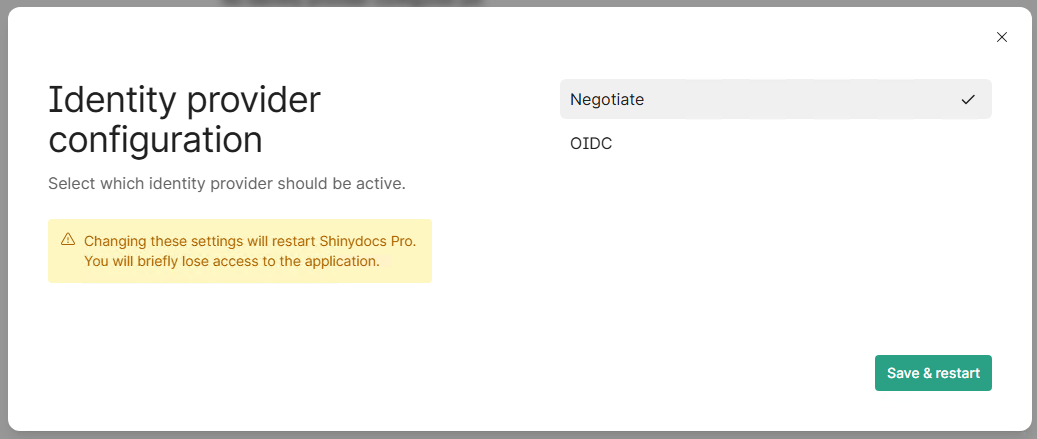
Shinydocs Pro Control Center supports the following identity providers to authenticate users and manage roles for access:
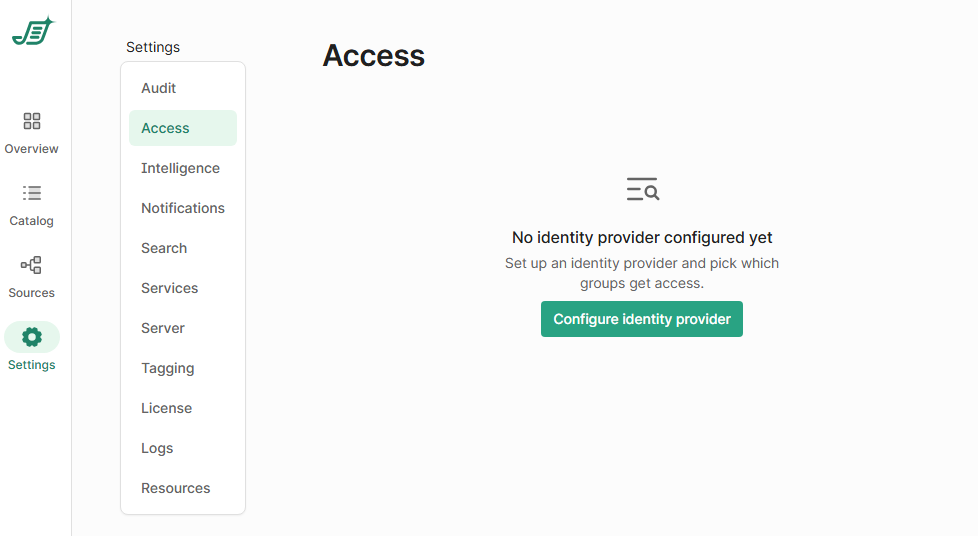
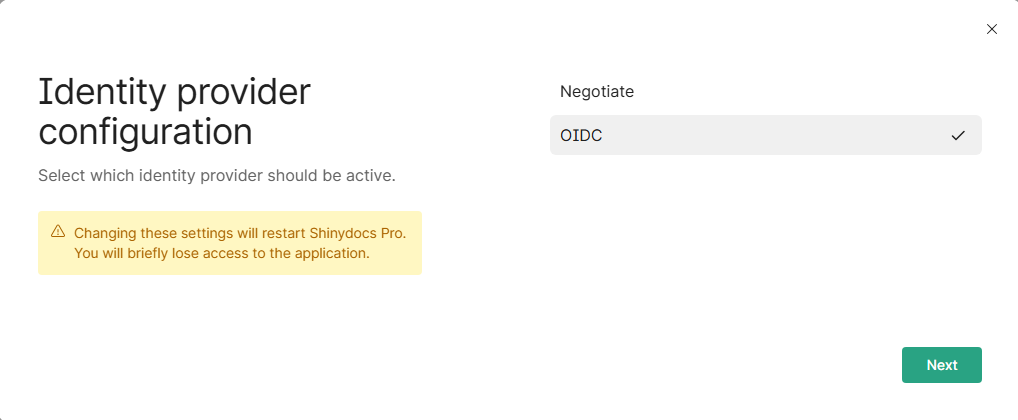
Click Configure identity provider
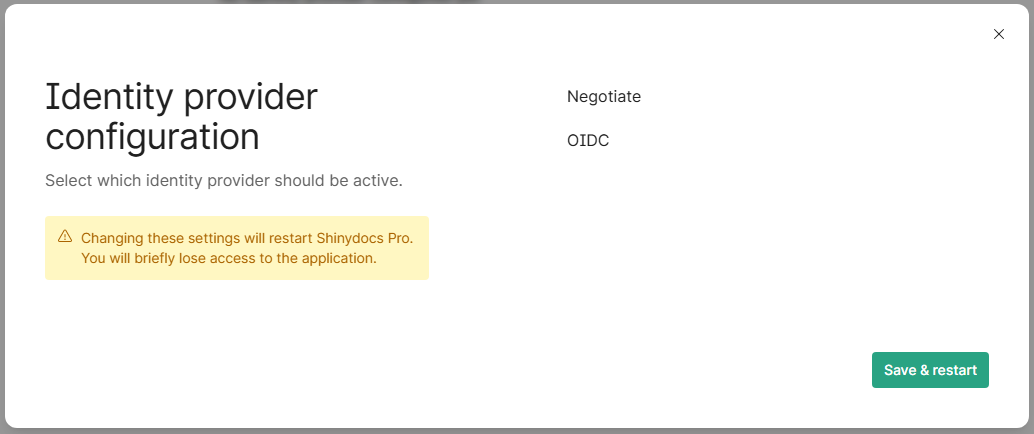
Select the provider you want to use
None (for testing and troubleshooting)
No authentication is required. Anyone who can reach Shinydocs Pro can access it without verifying their identity.
Because no user identity is established, audit entries in the Control Center will show actions as Anonymous. You will still see what happened, but not who did it.
This option is not secure and should only be used for local testing, demos, or short-term troubleshooting where authentication would get in the way.
Negotiate (Active Directory users & groups) - Default
Negotiate uses Windows Integrated Authentication and relies on Kerberos to automatically identify users who are already signed in to your Windows domain.If Shinydocs Pro and your users are part of the same Active Directory environment, authentication is seamless. Users are signed in automatically with their domain account and do not see a login prompt.
Audit entries will include user names, and access can be controlled using Active Directory users and groups.
Use this option when:
Shinydocs Pro is deployed on-premises or in a domain-joined environment
Users authenticate with Windows accounts
You want simple, frictionless sign-in and AD-based access control
You do not need external or cloud-based identity providers
OpenID Connect (OIDC) (Entra ID or similar providers)
OpenID Connect is a modern authentication standard built on OAuth 2.0. Shinydocs Pro trusts an external identity provider to authenticate users and confirm who they are.This option is commonly used with Microsoft Entra ID (formerly Azure AD), but it also works with other OIDC-compatible providers. Users sign in through the provider’s login page, and Shinydocs Pro receives verified identity and role information.
Audit entries include user identities, and access can be managed using roles or groups defined in the identity provider.
Use this option when:
Users are not domain-joined or are remote
You are using cloud or hybrid identity (Entra ID, SSO, MFA)
You want consistent authentication across multiple applications
You need modern security features like conditional access or multi-factor authentication
Recovery
If you're locked out of Shinydocs Pro Control Center because of a configuration issue, you can use the appsettings.json file to override the settings temporarily. Follow these simple steps to recover access.
Step 1: Locate the appsettings.json File
Go to the install directory for Shinydocs Pro Control Center.
The path is:
[Drive]:\[Install directory]\Shinydocs Professional\ControlCenter
Open the
appsettings.jsonfile using a text editor like Notepad.
Step 2: Understand the Overrides
The settings in appsettings.json can override your database configuration. Only use these for recovery purposes.
Each section is commented out with // to prevent it from running. You'll remove the // to activate the section you want to use.
Here’s what each section does:
Negotiate Authentication
CODE,"IdentityProvider": { "Negotiate": { "Enabled": true } }Uncomment this section to enable Negotiate authentication.
Set
"Enabled": falseto disable all authentication temporarily, which lets you access the Control Center without any login.
OpenID Connect (OIDC) Authentication
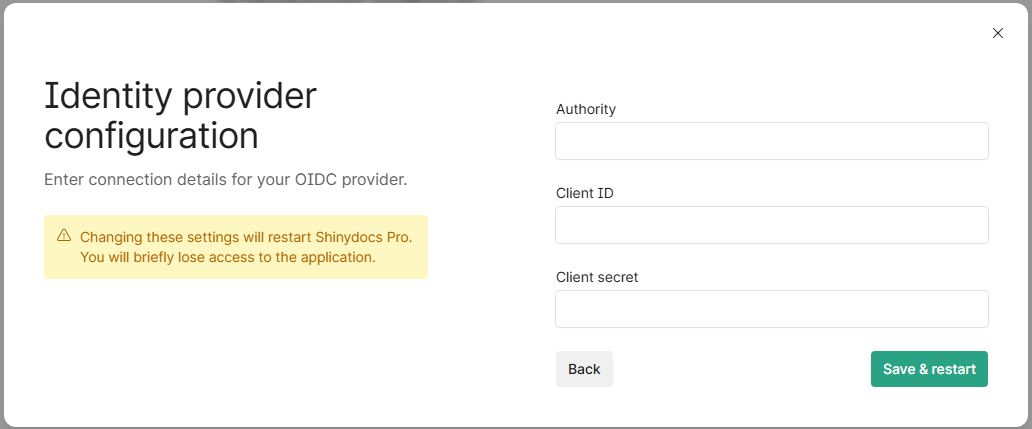
CODE,"IdentityProvider": { "Oidc": { "Authority": "", "ClientId": "", "ClientSecret": "" } }Uncomment and fill in these values to override OIDC settings for Azure/Entra.
Authority: Your OpenID Connect authority URL.
ClientId: The Client ID from your Azure/Entra app registration.
ClientSecret: The Secret Key from the app registration.
Access Roles (OpenID)
CODE,"Access": { "HasControlCenterAccess": [] }Uncomment this section and add roles to override which Active Directory (AD) or OpenID roles can access the Control Center.
You can add multiple roles by putting them in the brackets as a list.
Step 3: Save your changes and restart
Once you have saved the file, restart the Shinydocs Control Center service. Once you navigate to the Control Center home page, your new settings will be applied. You may need to clear your browser's cache.
If you are still unauthorized, that means your configuration did not work, please check the Control Center logs for more details. You can set negotiate to false to disable authentication (details below) if you need to investigate the issue further.
Step 4: Fix your configuration
The override is a temporary solution. Shinydocs Pro Control Center will display a warning in the Settings > Access section if you are using the override. You need to properly configure your Negotiate setup or OpenID in the Contol Panel UI (Settings > Access). Before saving your changes, you will need to add the comments back to the settings file and then save your changes in the Control Center UI. Shinydocs Pro Control Center will restart automatically with your new configuration.
// This configuration overrides the database configuration
// ONLY USE IN RECOVERY SCENARIO ⬇
/*
,"IdentityProvider": {
"Negotiate": {
"Enabled": true
}
}
*/
/*
,"IdentityProvider": {
"Oidc": {
"Authority": "",
"ClientId": "",
"ClientSecret": ""
}
}
*/
/*
,"Access": {
"HasControlCenterAccess": [],
"HasSearchAccess": []
}
*/Example Scenarios
Scenario 1: You want to disable all authentication to access the Control Center directly.
Uncomment Negotiate section.
Set
"Enabled": false.Leave all other sections commented out.
,"IdentityProvider": {
"Negotiate": {
"Enabled": false
}
}Scenario 2: You need to override OpenID Connect (OIDC) settings temporarily.
Uncomment OIDC section.
Fill in the
"Authority","ClientId", and"ClientSecret"with the correct values.Leave Negotiate and Access sections commented out unless you need to change them as well.
,"IdentityProvider": {
"Oidc": {
"Authority": "https://login.microsoftonline.com/your-tenant-id",
"ClientId": "your-client-id",
"ClientSecret": "your-client-secret"
}
}Scenario 3: You want to change which AD/OpenID roles have access to the Control Center.
Uncomment Access section.
Add roles to the
HasControlCenterAccessarray (e.g.,"HasControlCenterAccess": ["RoleName1", "RoleName2"]).Leave Negotiate and OIDC sections commented out unless you also need to change authentication settings.
,"Access": {
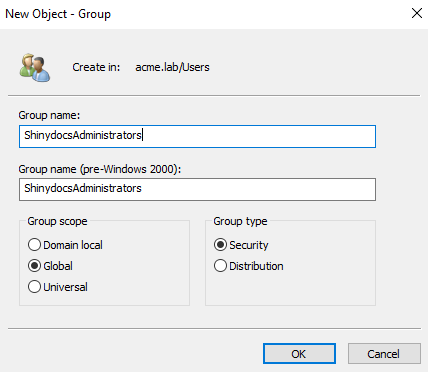
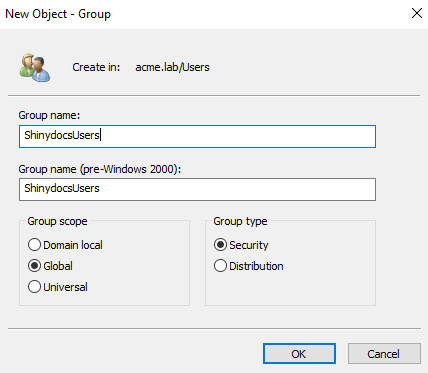
"HasControlCenterAccess": ["ShinydocsAdmin", "ShinydocsUser"]
}Scenario 4: You need to enable Negotiate (Windows authentication) again after disabling it.
Uncomment Negotiate section.
Set
"Enabled": true.Leave OIDC and Access sections commented out if you don't need to override them.
,"IdentityProvider": {
"Negotiate": {
"Enabled": true
}
}Troubleshooting
401 Unauthorized after disabling negotiate due to being locked out.
This is a browser cache issue. Either close your browser and all windows completely or:
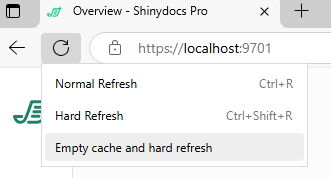
Press the F12 key in Edge or Chrome to bring up Dev Tools
Right-click the browser refresh icon and select Empty cache and hard refresh
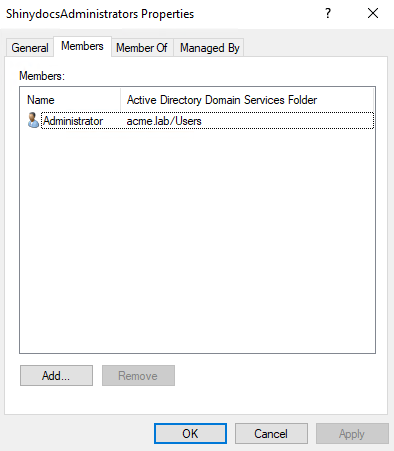
My Active Directory groups are not showing in the groups autocomplete field.
Windows will cache AD groups on logon, and if these groups are created while the server is on, the groups will not resolve properly. To fix this, simply restart the Shinydocs Pro server and the groups should appear in the dropdown. You may have to type in the first 3 letters to see it if you have many groups.
All of my settings and configuration are right but I’m still getting 403 unauthorized
First, make sure your current account (type
whoamiand press enter in CMD to see the account you are currently logged into Windows as. Make sure that account is in the group you assigned to Control Center access.Verify the server is still trusted by the domain
On the server running Shinydocs Pro, open PowerShell as administrator
Run Test-ComputerSecureChannel, if it responds with True the server is trusted and part of the domain
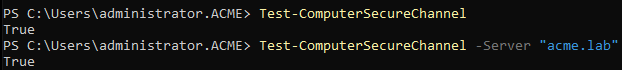
If it returns False, the server Shinydocs Pro Control Center is installed on is no longer trusted by the domain and will need to be resolved before proceeding
More information on this command and how to repair the connection can be found here: Test-ComputerSecureChannel (Microsoft.PowerShell.Management) - PowerShell | Microsoft Learn
Try restarting the server Shinydocs Pro Control Center is installed on