Unable to connect to URL
Problem
When adding a Content Server URL to the Content Source, you receive “Unable to connect to URL”, when it is an HTTPS connection, using a keystore/truststore.
In the tomcat-stdout file, you will see:
ERROR com.shinydocs.modules.contentserver.operations.ContentServerBaseOperations - Error connecting to server. Reason : Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-emptyIn the shinydrive-verbose log, you may also see:
ERROR com.shinydocs.modules.contentserver.operations.ContentServerBaseOperations - Error connecting to server. Reason : Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-emptyThose are pointing to issues with the certificate store, or configuration within Tomcat/Java, to the keystore being used, invalid certs in the keystore file, or invalid user/password being used.
Solution
Receiving "the trustAnchors parameter must be non-empty" when adding HTTPS SSO to Shinydrive.
Step-by-step:
Ensure the login/password is valid in the tomcat server.xml file
Ensure the location of the current keystore is noted in the Tomcat file
Ensure that the truststore is also being pointed to (in most cases, the same keystore is also the truststore)
There are two ways to complete this. One way is modifying the server.xml, and the other is adjusting the java options in Tomcat.
Modify the Tomcat java options:
To run Shinydrive server on HTTPS, use the PFX file created by the team maintaining the certs on the company side. Add these two lines in the Java Options in Tomcat:
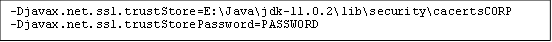
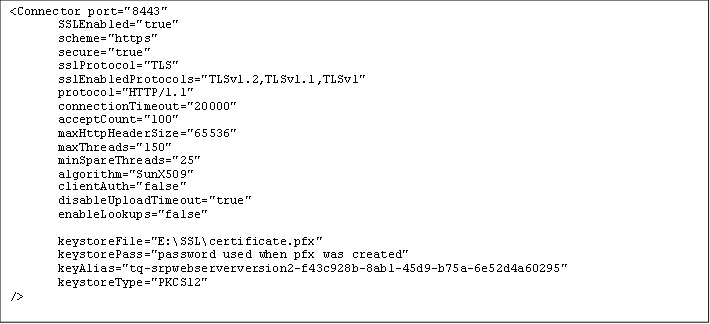
Edit the Tomcat server.xml (found in the <Tomcat>\bin\ folder, after creating a backup file first):
All of the steps above make it so that clients can connect to the Shinydrive server via HTTPS.
Connecting from Shinydrive to a secure (HTTPS) Content Server
In order for Shinydrive Server to then connect to OTCS over HTTPS, create a copy of the current cacerts file and then import your organization's Certificate Authority. This may be a .cer or a .crt file, and will ensure Shinydrive trusts the certificates from the Content Server or any other server with certs (issued by a Certificate Authority) with these commands.
To begin open a Command Prompt (Windows) as Administrator and navigate to the Java folder that your Tomcat is relying upon:
i.e. cd "C:\Program Files\Eclipse Adoptium\jdk-11.0.21.9-hotspot\lib\security"Ensure keytool is available, it should be included in the PATH if Java has been properly installed.
C:\Program Files\Eclipse Adoptium\jdk-11.0.21.9-hotspot\lib\security> keytool.exe
Key and Certificate Management Tool
Commands:
-certreq Generates a certificate request
-changealias Changes an entry's alias
-delete Deletes an entry
-exportcert Exports certificate
-genkeypair Generates a key pair
-genseckey Generates a secret key
-gencert Generates certificate from a certificate request
-importcert Imports a certificate or a certificate chain
-importpass Imports a password
-importkeystore Imports one or all entries from another keystore
-keypasswd Changes the key password of an entry
-list Lists entries in a keystore
-printcert Prints the content of a certificate
-printcertreq Prints the content of a certificate request
-printcrl Prints the content of a CRL file
-storepasswd Changes the store password of a keystore
-showinfo Displays security-related information
Use "keytool -?, -h, or --help" for this help message
Use "keytool -command_name --help" for usage of command_name.
Use the -conf <url> option to specify a pre-configured options file.Ensure you back up the current certificate file, typically named ‘cacerts’ though you may find an alternate filename, i.e. cacertsCORP, etc. Ensure you are in the \lib\security folder and copy the file:
copy cacerts. cacerts.bak
or
copy cacerts. cacerts_YYYY-MM-DD.bakYou will need to determine where your certificates, cer/crt files, are located. In this example we’ve collected the files in E:\SSL. We’ll construct the command line:
keytool.exe -import -keystore cacerts -file E:\SSL\corporate.crt -alias "Corporate SSL root ca"
keytool.exe -import -keystore cacerts -file E:\SSL\issuing.cer -alias "Corporate issuing ca"The default password for a cacerts is ‘changeit’ but it is advisable to change the password of the cacerts file:
keytool.exe -storepasswd -keystore cacerts** DO NOT MISPLACE THIS PASSWORD **
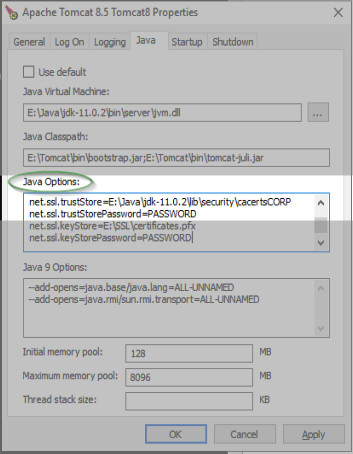
Then on the Java Options I added these two lines:
-DjavaX.net.ssl.trustStore=<JavaHome>\lib\security\cacerts
-DjavaX.net.ssl.trustStorePassword=*********The <JavaHome> would match your java location, i.e. C:\Program Files\Eclipse Adoptium\jdk-11.0.21.9-hotspot
The ********* would represent the password you set earlier.
The Java Options section ends up looking like this:
2. Modify the Tomcat server.xml to add the truststore line instead:
Edit the Tomcat server.xml (found in the <Tomcat>\bin\ folder, after creating a backup file first):
<Connector port="8443" maxThreads="500"
scheme="https" secure="true" SSLEnabled="true" acceptCount="500"
keystoreFile="/apps/content/certificates/keystore.ks" keystorePass="keystorepass"
truststoreFile="/apps/content/certificates/truststore.ks" truststorePass="truststorePassword"/>The above example may appear differently, additional entries for example, what is required is to add the truststoreFile line, as that will then ensure both of the keystore and truststore point to the same file to ensure that only one file needs to be updated in any future certificate updates.
For reference for further Tomcat configuration, please see these other articles:
Apache Tomcat 8 (8.5.88) - SSL/TLS Configuration How-To
